Information Technology Specialist
204 Hickory Oak Hollow
Cumming, GA 30040
Mon-Fri 9am-6pm
Evenings & Saturday by Appointment
Phone 470-253-0547
Email Gary at GaryHelm.Net
Near Me: Cumming Georgia, Forsyth County GA, Dawsonville GA, Gainesville GA, Dahlonega GA, Lake Lanier, Free Home GA, Ball Ground GA, Johns Creek GA, Milton GA

Internet and Computer Safety
Cybersecurity
Staying Safe on the Internet and keeping our devises secure is not an easy challenge.
However, there are simple things you can do to be reasonably safe.
First, What is Cybersecurity?
Cybersecurity refers to best practices and technologies used to protect us, our systems and our information against the malicious activity of criminals, natural and man-made disasters, hardware failures, and just simple mistakes.
Cybersecurity focuses on six primary areas:
Identify Risk
What are your risk? Most of use instantly think of getting a virus, getting hacked or scammed.
Human error, being misinformed or uninformed are the greatest risks.
Internal risks - employee theft
External risks - "bad actors"
Intrussion - "digital breaking and entering", corporate sabatoge,
Outdated hardware software that has not been updated.
Using default or weak password
Physical risks - lost or stolen property
Disaster Events - fire, flood, hurricane, tornado, loss of power, loss of internet, hardware failure.
It is not a question of if something bad will happen, it is a question of when.
Prevent Threats
Can you prevent something happening, or prevent a problem being worse than it could be?
Yes, there are things you can do.
It should go without saying: Use Security Software and Services, and Best Practices. Be Aware of what you are doing, what you click on, and where you are.
Be Proactive about Preventative maintenance
Have a plan. What are you going to do when (not if) something happens. Have a backup, have a secondary means or maintining operations.
Change default user name and passwords on modems and routers. All default user names and passwords are readily available on the internet. And update modem and router firmware regularly.
Use secure passwords. There are lists of most commonly used passwords readily available on the internet.
And password discovery software combined with AI can easily detect any eight character password in under one hour.
Use two-step authentication whenever possible.
Keep your firmware, operating system and other software up-to-date. Updates frequently include "security updates" needed to keep bad-actors out.
Learn How to Recognize scams, spam, phishing and other attempts to obatin access to your systems and information.
For more information about these go to my Cybersecurity Awareness Month
Consider adding a firewall (or firewalls) between you and the outside world.
Segment your network, don't give everyone administrative control .. Most modems/router combinations have a setting to have primary and guest WiFi connections, use them. Consider adding a second router to further segment network connections.
Use a good VPN service whenever connected to the Internet, especially on public WiFi connections.
"Disasters" happen. A disaster does not have to be a hurricane, flood, fire or a software company sending out a bad update. For some a disaster can be a hardware failure, a computer, server or service quits working.
Some of the recent incidents I wondered why companies were not prepared. Why was there not a "secondary location" to operate from.
Have Backups. Online backup services are an excellent way to manage backups, and they provide that "secondary location" to some extent.
Else, use a local backup such as an external drive, or cloan drives for easy replacement. Use full backups and incramental backups.
Do Not rely on "syncronized" backups as an attack on the primary system can corrupt the backup with the problem you are experiencing.
Detect Problems
How do you detect a problem, potential problem, or a problem that is about to get worse?
Most of us use: "Things aren't working right", don't sound right, don't feel right, all the way to the obvious "It isn't working".
Check your computer logs for warnings and errors, or periodically have someone do that for you.
Check firewall logs to detect suspicious activity.
Consider "Penetration Testing" to discover systems and user weaknesses.
Consider software that monitors activity on you network.
Most of us can't have our systems monitored 24/7/365 to detect problems such as intrusion detection - as some should -
Small businesses and Home users are targets for hackers as well and some security suites include some intrusion or suspicious activity features.
Mitigate Damage
The First Step in Mitigating Damage is to be prepared, have a plan, and work the plan.
Disconnect - turn off the device that has been infected, breached or compromised.
Notify banks, credit companies and others as needed about problems or possible problems.
Monitor your accounts for suspicious activity, and monitor for accounts being created that you did not.
Change all your passwords on all your internet accessable accounts.
Get someone who knows what they are doing, a professional to help you remove any potentially unwanted software and malware from you system(s).
Report Incidences
Reporting cyber-crimes helps make the Internet a safer place for you and everyone.

Report Cyber-Crimes & Cyber-Criminals
Examples of Cyber-Crimes
- Phishing Scam
- Impersonation
- Identity Theft
- Stalking Online
- Cyberbulling
- Tech Support Scams and Phantom Hackers
- Unauthorized Access - Hacking
- Corportate /Business Espionage
- Intellectual Property Rights Infringement
- Ransomware, Malware, Viruses
- Fraud
FBI's Internet Crime Complaint Center (IC3) .. report crimes
FBI Complaint Center
FTC Avoiding and Reporting Scams
FTC.gov Report Scams
Stay Safe Online - Report Cybercrime
Stay Safe Online - Report Cybercrime
Secure-Our-World-Reporting-Cybercrime-Tip-Sheet
DHS Reporting Cybercrime Complaint
Secure-Our-World-Reporting-Cybercrime-Tip-Sheet.pdf
Secure-Our-World-Reporting-Cybercrime-Tip-Sheet
Georgia Bureau of Investigation
GBI Specialized Units
Georgia Emergency Management and Homeland Security Agency
Georgia Report Cyber-Crime & Threats
Federal Bureau of Investigation
FBI.gov
Department of Homeland Security
Department of Homeland Security
Federal Communication Commission
FCC.gov
Transportation Security Administration
TSA.gov
Federal Trade Commission
FTC.gov
Recovery
Recovery can be a slow "painful" process. In part it depends on how prepared you are.
As we have seen and experienced in recent months, even a security update can cause havock across industries.
Is there a backup plan for unexpected man-made or natural disaster.
Examples One and Two:
When CrowdStrike pushed out a security update, and Microsoft passed the update along to clients, it affected industies around the globe.
When Hurricane Helene dumped masssive volumes of rain over western North Carolina, families, communities and businesses were devistated.
One business in particular that had a regional affect. Ingles groceries had a lot of their technology centered in one location. When
that location was damaged, Ingles was unable to conduct business as usual for days.
In each of these two examples, had companies had secondary locations (effective backup systems) to simply switch over to and use, neither of events would have been so disruptive.
By having a secondary location that was un-affected by the man-made or natural disaster, network administrators could have adjusted settings from the primary to the secondary network.
These steps would have been costly up-front, but much less disruptive and costly in the long-run.
Most of us do not need to go to these extremes to be prepared but basic precautions and preparedness can be less disruptive and costly in the long-run.
Additional Cybersecurity Information
For some practical Best Practices for staying safe on the Internet visit my Cybersecurity Awareness Month page.
Additional Resources
It is not a question of "If", it is a question of "When".Be Prepared for a Cyberattack
General Information
DHS - Cybersecurity Preparedness web
Be Prepared Tip Sheet
DHS - Be Prepared Cyberattack Tip Sheet pdf
What to do "When" anything happens
NIST - Computer Security Incident Handling Guide pdf
Cybersecurity Survival Guide
NCA - Cybersecurity Survival Guide web
Ten Basic Steps you can take to help prepare for cyberattacks.
NCA - Online Safety Basics web
Stop Ransomware
Ransomware comes in a variety of forms, from simply taking over your computer screen to encrypting your hard drive so they have to provide you a code to turn on your computer.The common demand is you pay a ransom to get use of your computer back.
CISA - Stop Ransomware August 29, 2024 Advisory pdf
CISA - Stop Ransomware Website
Back IT Up
"Things Happen" - When your computer, table, phone or other device quits working, having a backup can save the day.
When your systems are compromised by a cyber-attack or failed update, having backup systems can save the day.
Back It Up
my blog - Back It Up
US-CERT Data Backup Options
US-CERT - Data Backup Options pdf
NIST/NCC0E MSP Protecting Data Extended
NIST/NCC0E - MSP Protecting Data Extended pdf
Social Engineering
Social Engineering uses common behavioral responses in an effort to get you to do something "they" want.Social Engineering appeals to our emotions, such as: fear, greed, loyalty, curosity, obediance, anger, hatred, desire to help, urgency, trust.
CISA - What is Social Engineering & How Does it Work web
WI-Fi Security
Using a VPN service can help protect you from hackers by hiding your location and encrypt data.
Use VPN "Pull the Shades Down"
NCA - VPN Pull the Shades Down web
Protect your home Wi-Fi network
How to Secure Your Home Wi-Fi
Your router has a default user name and password. If it is not changed, there are lists of default passwords on the Internet.
FTC - Secure Your Wi-Fi Network web
Social Media Scams
Social Media Poster
Social Media Poster
Take Back Control of a Social Media Account
HAS Links to Facebook, YouTube, Google, WhatsApp, Instagram, TikTok, LinkedIn, SnapChat, Reddit, Pinterest, X (Twitter), Discord, Blue Sky, Mastodon
NCA - Take Control of Social Media web
That Hard to find 'Report Compromised Facebook Account' page
FB - Report Hacked Facebook Account web
Facebook Help Center
Hacked and Fake Accounts (Hacked and Impersonation on Facebook)
FB - Facebook Help web
Tech Support Scams
Federal Trade Commission advice "How to Spot, Avoid and Report Tech Support Scams"
FTC - Avoid Tech Support Scams web
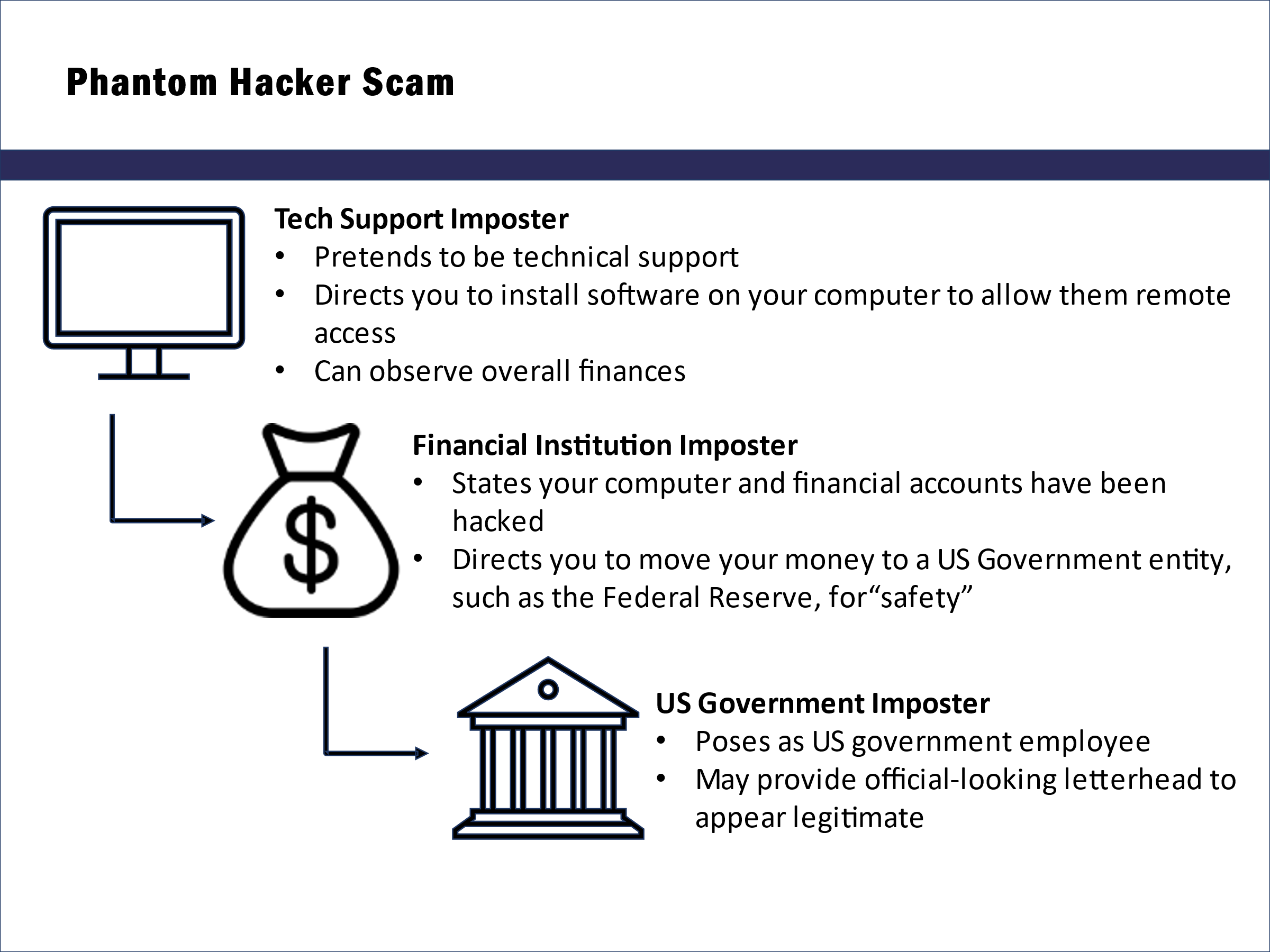
MULTI-LAYER TECH SUPPORT SCAM - Phantom Hacker Scam
What is a Phantom Hacker Scam
A "Phantom Hacker Scam" is the combination of three old scams:
- You get a popup on your computer, email, text or phone call, telling you there is a problem with your computer, and "tech support" needs in your computer.
- You are then told there is a problem with some financial account and you are transfered to "financial support", typically a person claiming to be with your bank.
- You are tne transfered to a "government official" to report the crime against you.
During this time you are at risk of loosing your life savings.
- Phantom Scammer Hacker #1
The Imposter claims to be tech support - Phantom Scammer Hacker #2
The Imposter claims to be financial institution - Phantom Scammer Hacker #3
The Imposter claims to be US Gov Official
The scam begins when you respond to the popup, email, text or phone call.
NO Tech Support, No Financial Institution, or Goverment Agency will contact you in this manner.
SENIORS & Elders
"Phantom Hacker"
is a MULTI-LAYER TECH SUPPORT SCAM
Highly Organized, Highly Proficient
- phase 1 Tech Support IMPOSTER
- phase 2 Financial Institution IMPOSTER
- phase 3 US Gov Official IMPOSTER
FBI/ic3 - Phantom Hacker web
FBI/ic3 - 2023 Elder Fraud Report pdf
Increase of Tech Support Scams targeting Older Adults
FBI/ic3 - Increase in Tech Support Scam webs
Children, Students and Families
Tip Sheet for Parents to Help Children Use Technology SafelyCISA - Secure-Our-World-Raising-Digital-Citizens-Tip-Sheet pdf
DOJ/OVC - Internet Crimes Against Children web
Artificial Intellegence
Secure-Our-World-Using-AI-Tip-SheetCISA - Secure-Our-World-Using-AI-Tip-Sheet pdf
+81% of Passwords Hacked by Ai in Under 1 Hour
Workplace Security & Training
Puzzels and Games
Fun Ways to Learn about CybersecurityCybersecurity-Awareness-Month-2024-Puzzles
NCA - 2004 Cybersecurity Puzzels pdf
CISA Cybersecurity Games
CISA Cybersecurity Games web
Cybersecurity Video Library
Short Helpful Videos about Best Practices and Internet SecurityCybersecurity Video Library
Back to Top
How to Get Involved
Back to TopBlog and Tools
Tools
Random Password Generator
Security
AI-Generated Deepfake Scams +81% of Passwords Hacked by Ai in Under 1 Hour Back IT Up Is Remote Support Right for You? Is VPN Right for You? Best Practices Potentially Unwanted Programs (PUPs) Don't Call that 800# It's a Scam Unlock "Lock My PC" Scam Scam Alert