Information Technology Specialist
204 Hickory Oak Hollow
Cumming, GA 30040
Mon-Fri 9am-6pm
Evenings & Saturday by Appointment
Phone 470-253-0547
Email Gary at GaryHelm.Net
Near Me: Cumming Georgia, Forsyth County GA, Dawsonville GA, Gainesville GA, Dahlonega GA, Lake Lanier, Free Home GA, Ball Ground GA, Johns Creek GA, Milton GA
What is Passwordless Authentication
How can a Passkey be beneficial?
Apple, Google and Samsung have been using Passwordless identification for sometime with facial, fingerprint or personal identification number (PIN) to login and verify your identity. And you can use that verification to log into other online accounts as well.
Those are passwordless authentication.
Facial recognition and fingerprint recognition have been around for decades and have gained popularity with Apple, Google and Samsung phones, tablets and computers. Just look at your appliance or touch the sensor and you’re signed in.
So what is the news about Microsoft going passwordless about?
Microsoft has been using your PIN or password to log into computers and accounts for years. Microsoft is simply doing away with the password. Microsoft recently announced it will go passwordless to sign into Microsoft accounts, such as MS (Office) 365.
But Microsoft appears to not have the capability of using that PIN to sign into other online accounts.
That is where a Passkey may be beneficial for you.
Not all hardware is manufactured with passwordless technology built in to sign into online accounts. To add passwordless technology to appliances without it built in, a Passkey can be purchased and attached wireless or by USB. Some Passkeys use a PIN, fingerprint or both.
You may not need a passkey to log into your Microsoft accounts but there are definite security benefits.
Passkeys further illustrate the benefit of passwordless technology.
Passkeys provide three extra layers of security.
- First it has a local code giving you access to the hardware.
- Second when you sign into an online account the passkey sends a private code linked to the local code verifying it is being sent by your Passkey.
- Third, unlike Passwords and 2FA codes that are sent as open text, and if intercepted can be read by cybercriminals. Passkeys use encrypted codes so it is much more secure, cannot be read and are not stored on the server.
Additional Resources
It is not a question of "If", it is a question of "When".Be Prepared for a Cyberattack
General Information
DHS - Cybersecurity Preparedness web
Be Prepared Tip Sheet
DHS - Be Prepared Cyberattack Tip Sheet pdf
What to do "When" anything happens
NIST - Computer Security Incident Handling Guide pdf
Cybersecurity Survival Guide
NCA - Cybersecurity Survival Guide web
Ten Basic Steps you can take to help prepare for cyberattacks.
NCA - Online Safety Basics web
Stop Ransomware
Ransomware comes in a variety of forms, from simply taking over your computer screen to encrypting your hard drive so they have to provide you a code to turn on your computer.The common demand is you pay a ransom to get use of your computer back.
CISA - Stop Ransomware August 29, 2024 Advisory pdf
CISA - Stop Ransomware Website
Back IT Up
"Things Happen" - When your computer, table, phone or other device quits working, having a backup can save the day.
When your systems are compromised by a cyber-attack or failed update, having backup systems can save the day.
Back It Up
my blog - Back It Up
US-CERT Data Backup Options
US-CERT - Data Backup Options pdf
NIST/NCC0E MSP Protecting Data Extended
NIST/NCC0E - MSP Protecting Data Extended pdf
Social Engineering
Social Engineering uses common behavioral responses in an effort to get you to do something "they" want.Social Engineering appeals to our emotions, such as: fear, greed, loyalty, curosity, obediance, anger, hatred, desire to help, urgency, trust.
CISA - What is Social Engineering & How Does it Work web
WI-Fi Security
Using a VPN service can help protect you from hackers by hiding your location and encrypt data.
Use VPN "Pull the Shades Down"
NCA - VPN Pull the Shades Down web
Protect your home Wi-Fi network
How to Secure Your Home Wi-Fi
Your router has a default user name and password. If it is not changed, there are lists of default passwords on the Internet.
FTC - Secure Your Wi-Fi Network web
Social Media Scams
Social Media Poster
Social Media Poster
Take Back Control of a Social Media Account
HAS Links to Facebook, YouTube, Google, WhatsApp, Instagram, TikTok, LinkedIn, SnapChat, Reddit, Pinterest, X (Twitter), Discord, Blue Sky, Mastodon
NCA - Take Control of Social Media web
That Hard to find 'Report Compromised Facebook Account' page
FB - Report Hacked Facebook Account web
Facebook Help Center
Hacked and Fake Accounts (Hacked and Impersonation on Facebook)
FB - Facebook Help web
Tech Support Scams
Federal Trade Commission advice "How to Spot, Avoid and Report Tech Support Scams"
FTC - Avoid Tech Support Scams web
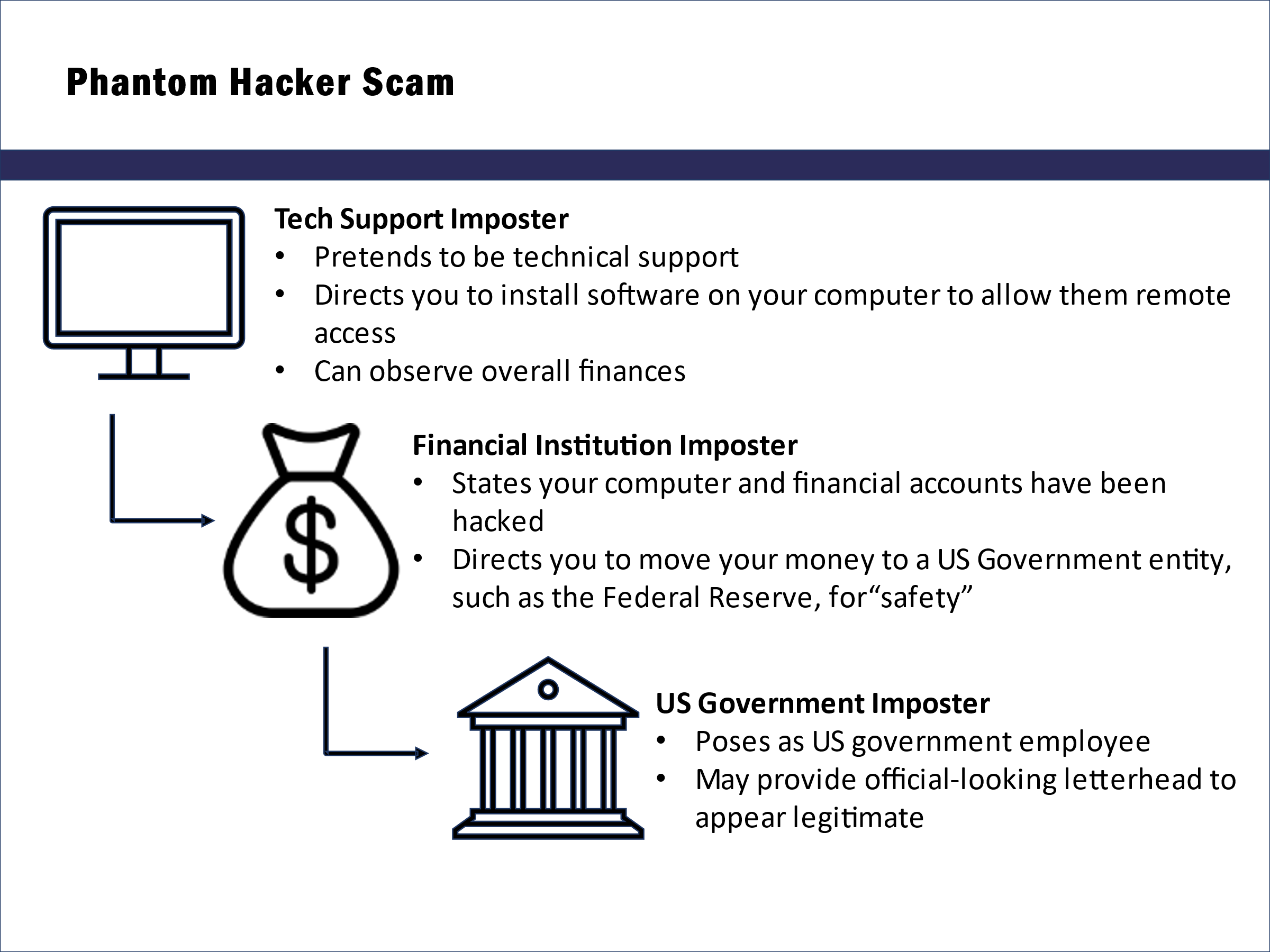
MULTI-LAYER TECH SUPPORT SCAM - Phantom Hacker Scam
What is a Phantom Hacker Scam
A "Phantom Hacker Scam" is the combination of three old scams:
- You get a popup on your computer, email, text or phone call, telling you there is a problem with your computer, and "tech support" needs in your computer.
- You are then told there is a problem with some financial account and you are transfered to "financial support", typically a person claiming to be with your bank.
- You are tne transfered to a "government official" to report the crime against you.
During this time you are at risk of loosing your life savings.
- Phantom Scammer Hacker #1
The Imposter claims to be tech support - Phantom Scammer Hacker #2
The Imposter claims to be financial institution - Phantom Scammer Hacker #3
The Imposter claims to be US Gov Official
The scam begins when you respond to the popup, email, text or phone call.
NO Tech Support, No Financial Institution, or Goverment Agency will contact you in this manner.
SENIORS & Elders
"Phantom Hacker"
is a MULTI-LAYER TECH SUPPORT SCAM
Highly Organized, Highly Proficient
- phase 1 Tech Support IMPOSTER
- phase 2 Financial Institution IMPOSTER
- phase 3 US Gov Official IMPOSTER
FBI/ic3 - Phantom Hacker web
FBI/ic3 - 2023 Elder Fraud Report pdf
Increase of Tech Support Scams targeting Older Adults
FBI/ic3 - Increase in Tech Support Scam webs
Children, Students and Families
Tip Sheet for Parents to Help Children Use Technology SafelyCISA - Secure-Our-World-Raising-Digital-Citizens-Tip-Sheet pdf
DOJ/OVC - Internet Crimes Against Children web
Artificial Intellegence
Secure-Our-World-Using-AI-Tip-SheetCISA - Secure-Our-World-Using-AI-Tip-Sheet pdf
+81% of Passwords Hacked by Ai in Under 1 Hour
Workplace Security & Training
Puzzels and Games
Fun Ways to Learn about CybersecurityCybersecurity-Awareness-Month-2024-Puzzles
NCA - 2004 Cybersecurity Puzzels pdf
CISA Cybersecurity Games
CISA Cybersecurity Games web
Cybersecurity Video Library
Short Helpful Videos about Best Practices and Internet SecurityCybersecurity Video Library
Back to Top
How to Get Involved
Back to TopBlog and Tools
Tools
Random Password Generator
Security
AI-Generated Deepfake Scams +81% of Passwords Hacked by Ai in Under 1 Hour Back IT Up Is Remote Support Right for You? Is VPN Right for You? Best Practices Potentially Unwanted Programs (PUPs) Don't Call that 800# It's a Scam Unlock "Lock My PC" Scam Scam Alert